How To Pick A Trustworthy Virtual Private Network (VPN)

Virtual Private Networks (VPNs) are becoming more and more common as something many people use or at least have heard about, but may not know a lot about how they work, what risks they carry, or what option is best for them. VPNs can be crucial for activists and civil society groups to protect themselves from outside actors attempting to view or steal private data, but it is just one of many tools that should be considered as part of a comprehensive cybersecurity strategy. This blog will give you an overview of the things you should be aware of when deciding to use a VPN and a few recommended tools to set you on the right path.
What is a VPN?
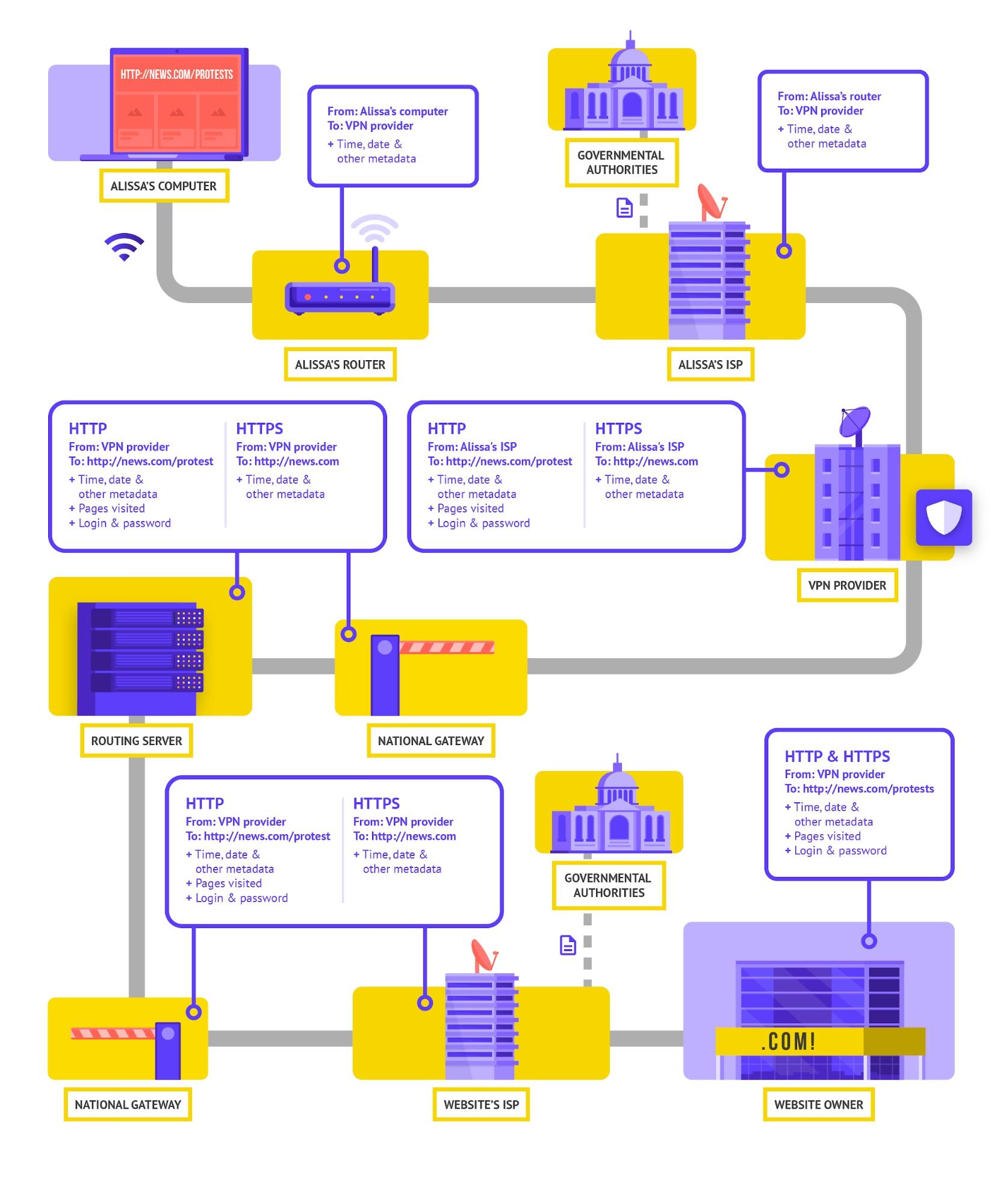
You can think of a Virtual Private Network, or "VPN" as a sort of tunnel that your internet traffic travels through. This tunnel hides your data from people who may be trying to surveil or block your internet traffic. Those people could be hackers, your network administrator, your Internet Service Provider (ISP), and anyone these groups might share your data with (such as law enforcement, the government). In other words, when browsing the internet using a VPN, it creates a private network over the public internet, which hides the actual IP address and encrypts all connections with the outside world. This gives the users a level of anonymity and makes it harder for someone to see what content you are looking at. VPNs can also avoid geoblocking, allowing users to access content that may only be accessible if accessing the internet from another country. Encrypting individual internet traffic to disguise a user's online identity makes it more difficult for third parties to track and steal online activity or data.
Limitations of VPNs
There are numerous benefits to using VPNs, but using a VPN does not make you completely anonymous online: your traffic is still visible to the operator of the VPN. Many VPNs on the market (especially free VPNs) sell your data rather than protect it. VPN providers may also be pressured to turn over data to government or law enforcement. Therefore, it is crucial to find a trustworthy VPN provider and read their privacy policy. When using a VPN, your ISP will still know that you are using a VPN, which might make your internet use suspicious. For more information on how to evaluate the trustworthiness of a VPN provider, visit NDI’s Cybersecurity Handbook for Civil Society Organizations.
Please note that, even if you trust your VPN provider, there is some browsing information that might not be private. For example, information you enter into a website, like your username, email or credit card information is shared with that website and could be exposed. Using Google Search while logged into your Google Account will share your search history with Google.
How to Choose a VPN
Don’t take our word for it. While this blog post lists VPN applications that DemTech most frequently recommends, learning how to distinguish trustworthy VPNs on your own is an important skill. The Electronic Frontier Foundation’s Surveillance Self-Defense (SSD) provides more comprehensive advice, but here are a few places to start:
- Do your homework. There is a LOT of misleading information and hyperbolic claims around VPNs. Try researching some trustworthy lists like Privacy Guides, Freedom of the Press Foundation, and Consumer Reports. You can also check reputable news sources for articles about the VPN you are thinking about using. Some VPNs will not work in certain places because they are blocked. Understanding what works in your context will help avoid wasted effort, and having a backup option downloaded to your device in case one gets blocked or stops working is never a bad idea.
- Look at the terms and conditions. Every reputable VPN should have a privacy policy and legal guidelines around how they handle law enforcement requests. They should also state when they had their last independent audit. Some key considerations you want to look for are, 1) that the VPN is subjected to regular security audits, 2) that the VPN does NOT sell or share user data, 3) that the amount of information required to sign up for the VPN is minimal, and 4) that the VPN uses a good encryption protocol (WireGuard, for example).
- Avoid “free” VPNs. Free VPNs are probably too good to be true. It costs money to operate a VPN, and if they aren't charging you much, they're likely making money another way, usually by selling your data or showing you advertisements. Exceptions to this rule include trustworthy VPNs that offer discounts or free access to nonprofits.
- Ask for help. When in doubt, consult a security professional. A good security professional will do more than just identify and use trustworthy VPNs, they will help create a security plan that takes into account all aspects of your safety, digital and physical, based on a detailed understanding of your threat environment.
Based on your answers to the questions above, you will likely find yourself with a number of good VPN options remaining to choose from. DemTech does not specifically endorse any particular VPN product over another (assuming it fits the criteria above), but just a few options often recommended to civil society, parliament and other democracy advocates include TunnelBear, which is available for free for users in restrictive environments through the company’s Bandwidth Support program. Mullvad, Outline, ProtonVPN and many other VPNs are great options too, just remember to do your research (as described above) before downloading!