Tips for Using Common Secure Online Messaging Apps

Editor’s Note: Things change quickly in the world of secure messaging, so some recommendations may be out of date at the time of your reading.
Collaboration and communication are the main foundation of building a successful work environment in any field. There are many ways for team members to communicate, and traditional email is insufficient for today's modern professional workplace. This is especially true for political and civil society groups involved in communicating sensitive information. These groups must make sure that they’re choosing the most secure tools to send information. This blog focuses on common messaging tools that can support secure messaging for civil society groups, parliaments, political parties, or election observers. No application is perfect, and every context is different so what works for one group may not for another. However, we hope this general guidance will help you to communicate more securely online.
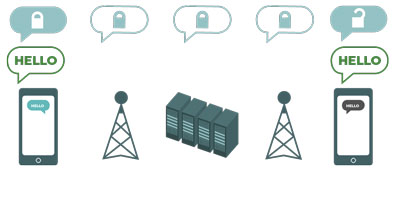 Diagram that shows how end-to-end encryption (E2EE) works.
Diagram that shows how end-to-end encryption (E2EE) works.When it comes to secure messaging, Signal is the app DemTech most commonly recommends to our partners because it does an excellent job of keeping private communications private. Unlike other apps on this list, Signal was designed specifically for the purpose of secure communication. This is done via encryption. You can think of encryption as scrambling a message and making it impossible to read, unless you have a key to unscramble it. All messages sent on Signal are end-to-end encrypted (E2EE). This means that only the person who sent the message and the person who receives the message have the “key” and are able to view the content of the message. The message is encrypted, or scrambled, in transit, and no one else, not even Signal, has the ability to read it.
It is important to remember that E2EE only protects the content of your communications, not the metadata. Metadata can be described as everything you need to communicate with others, except the content of your communications. Imagine metadata as an envelope; it contains information including the sender, receiver, and destination of a message.
Some services use transport layer encryption, or transport layer security (TLS), which protects messages as they travel between users’ devices and the messaging app/service’s servers. This is a lesser form of encryption because your messages are not encrypted when stored on the company’s servers. In this case, the company providing the messaging service, in addition to the message sender and receiver, also has access to the “key”.
Short Message Service (SMS) messages are not end-to-end encrypted, and they are stored unencrypted in your cellular provider’s systems. Messages are often only retained for several days, but they store metadata for even longer.
It is also important to understand that if your device is compromised by malware (or physically stolen and not protected with a strong passcode) no level of encryption can protect your private messages. So in addition to adopting secure messaging practices, it is essential to implement the best practices described in the Secure Devices section of our Cybersecurity Handbook.
With that, let’s compare the features and evaluate the security of some of the most popular apps out there. All of these apps are available for both iOS and Android phones.
Most Recommended: Signal
Signal is a fully open source platform developed by Signal Messenger LLC, a subsidiary of the non-profit Signal Foundation. In addition to E2EE, as mentioned above, Signal has advanced security features, like disappearing messages, which when enabled automatically delete messages after a customizable time period. The Sealed Sender feature adds another layer of protection to users by significantly limiting the amount of metadata, such as who sent the message and at what time, seen even by Signal itself.
Increased dependency on online communications throughout the pandemic resulted in a massive increase in Signal users in 2020, but the app still has a relatively small market share compared to the other apps on this list.
Another important security consideration is that Signal requires a phone number. This means that anyone intent on tracking your online footprint can see that you’re using Signal. A properly configured Virtual Private Network (VPN) can further obscure your internet usage and hide the fact that you are using Signal, but the fact that you are using a VPN may still be apparent.
Recommended with Caveats: WhatsApp
WhatsApp’s greatest strength is that many of your contacts likely already use it. This secure messaging platform, which is owned by the American company Meta (formerly Facebook), allows users to send text and voice messages (both to individuals and in group chats); make voice and video calls; and share images, documents, user locations, and other content for free. WhatsApp messages and calls are E2EE which makes it a secure messaging option. It is important to note, however, that WhatsApp does not protect metadata in the same way that Signal does.
WhatsApp also has a feature which allows users to back up all their messages to the cloud. While this can be useful, NDI strongly recommends disabling this feature. Using cloud backups essentially undoes the benefits of E2EE because it stores your sensitive messages in a cloud-based server, which can be hacked. This means that instead of only the sender and receiver being able to view the message, the message is on another platform that can be hacked. So be sure to turn off cloud backups, or at the very least enable WhatsApp’s new end-to-end encrypted backups feature. You can find simple how-to guides for configuring security settings for Android phones and for iPhones. However, even if you take these precautions, there is a risk that someone you message will not, which leaves messages between the two of you vulnerable to hacking.
Recommended for Teams: Google Chat
The world’s leading internet search giant, Google, also offers a communication and collaboration tool, which was initially designed for professional environments. Google Chat provides direct messaging and group conversations. Like Slack, Microsoft Teams, and Mattermost, the tool is increasingly being refined to support teamwork; so it has more built-in collaboration tools (like the Spaces feature, which allows teams to create and assign tasks, create grouped message conversations, and share files) than other secure messaging apps on this list. Google Chat can be accessed through chat.google.com or Gmail, and there are also mobile apps for each website. Slack was the original innovator of this “workspace” approach to messaging and has more features, customizations, and third-party integrations than Google Chat, but it does not have E2EE, instead using TLS to secure communications.
Google Chat allows easy E2EE communications within the Google Workspace ecosystem through a Google account, without requiring a mobile phone number. Google Accounts come with built-in security systems to detect and block threats like spam, phishing, and malware, but users can also control privacy settings in their Google Account settings and block and report people or Spaces manually when needed. Microsoft Teams and Mattermost, an open-source alternative, can both be made to enable E2EE but this feature is not turned on by default.
Least Recommended: Viber and Telegram
Some services, like Facebook Messenger, Viber, and Telegram, only offer end-to-end encryption if you deliberately turn it on (and only for one-to-one chats), so they are not good options for sensitive or private messaging, especially for an organization. Do not rely on these tools if you need to use end-to-end encryption, because it is quite easy to forget to change away from the default, less secure settings, and the settings of the people you are messaging can affect you as well. Viber claims to offer end-to-end encryption and disappearing messages and hidden chats features, but has not made its code available for review to outside security researchers. Telegram’s code has also not been made available for a public audit. As a result, many experts fear that Viber’s encryption (or Telegram’s “secret chats”) may be substandard and therefore not suitable for communications that require true end-to-end encryption.
However, Viber and Telegram are very popular platforms. If security is not a concern, they may be good choices for reaching large numbers of people. It is very important to be transparent with those you are contacting about the risks unsecure services pose to users.
